Blogs

Secure docker instance with basic Authentication | by secureITmania | Medium
Recently, I faced a challenge to deploy a docker web application with basic authentication. Instead…
Tags: cloudsecurity, docker, Infosec, DevOps, ReverseProxy

The Importance of Checking User-Agent Header Dependency in Penetration Testing | by secureITmania | Medium
In the world of penetration testing, it is crucial to employ the right tools and methodologies to u…
Tags: BugBounty, PenetrationTesting, Infosec, HackingTechnique

Learn and Earn with the Most Common Unsecured Methods of OTP Bypass Techniques: Unpacking the Pitfalls | by secureITmania | Medium
As the digital world expands, so does the importance of cybersecurity. One Time Passwords (OTP) hav…
Tags: SecureDevelopement, BugBounty, MFASecurity, OTPBypass, Infosec
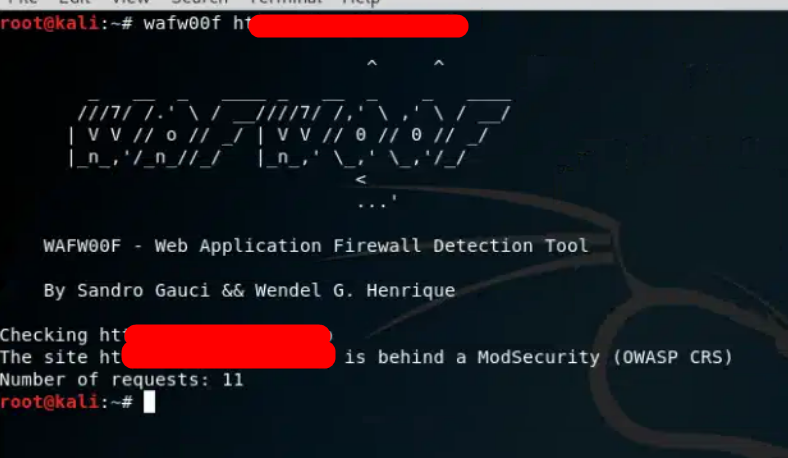
The Art of Identifying X$$ & WAF Bypass Fuzzing Technique | by secureITmania | Medium
Cross-site scripting (XSS) vulnerabilities are among the most common security issues in web applica…
Tags: XSS, WAFBypass, WAF, BugBounty, Infosec, Cross-Site Scripting

Never use the GET method for Sensitive Actions in Web App: Ft. CSRF | by secureITmania | Medium
With the introduction of the default “Samesite: Lax” feature, developers can now enhance the securi…
Tags: SecureDevelopement, CSRF, BugBounty, BrowserSecurity, Infosec

S3 bucket enumeration simplified. | by secureITmania | Medium
When conducting bug hunting and penetration testing, you might come across S3 bucket endpoints and …
Tags: AWS, Cloudsecurity, S3Bucket, BugBounty, Misconfiguration
Why Appropriate Content-Type Header Matters In REST API Security: Ft. JSON XSS | by secureITmania | Medium
Before diving into the specifics of the Content-Type header, let’s quickly recap what REST APIs are…
Tags: APISecurity, XSS, BugBounty, API, BugBounty

Weird “Subdomain Take Over” pattern of Amazon S3 | by secureITmania | entersoftsecurity | Medium
Thanks for huge response to my previous write-ups. Recently I participated in a Bug Bounty program …
Tags: cloudsecurity, aws, DNS, BugBounty